Personal Tool for Protection on the Net
Abstract
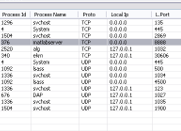
Every time a computer device connects to the Internet it is at risk. Data theft is one of the threats facing computers when they connect to the Internet. For a computer to connect to the Internet, it needs an IP address and a port address to send and receive data. When the data reaches the computer via a port, it needs to reach the process that requested this information, which is linked to that port. A process does all the internet connections by the compute. These processes need an approach to send and receive information, which is the ports themselves. The attacker uses this port to make a connection to the victim's computer to steal information. In such situations, support is crucially needed to prevent these attacks from affecting our system. This work develops a personal tool for helping users to protect themselves from external attacks. The proposed tool monitors the open ports and shows all the information about the processes that are used. The proposed tool can close the open port, kill the process associated with it, and delete the process. When closing this port, the attacker cannot have access to the victim's computer. The findings show that the proposed tool is highly efficient when it comes to computer protection. The experimental results also demonstrate that the features of the tool can be tuned to fit users’ interest.
Keywords
Full Text:
PDFReferences
Yuan, C., Du, J., Yue, M. and Ma, T. (2020) The design of large-scale IP address and port scanning tool. Sensors (Basel, Switzerland) 20 (16), 1-12.
Algaolahi, A. Q. M., Hasan, A. A., Sallam, A., Sharaf, A. M., Abdu, A. A. and Alqadi, A. A. (2021) Port-Scanning Attack Detection Using Supervised Machine Learning Classifiers. 2021 1st International Conference on Emerging Smart Technologies and Applications (eSmarTA). 10-12 Aug. 2021.
M. Lefoane, I. Ghafir, S. Kabir, and I. Awan, “Machine Learning for Botnet Detection: An Optimized Feature Selection Approachâ€. International Conference on Future Networks & Distributed Systems. Association for Computing Machinery, New York, NY, USA, 2021.
Ananin, E. V., Nikishova, A. V. and Kozhevnikova, I. S. (2017) Port scanning detection based on anomalies. 2017 Dynamics of Systems, Mechanisms, and Machines (Dynamics). 14-16 Nov. 2017.
I. Ghafir, V. Prenosil, A. Alhejailan and M. Hammoudeh, “Social Engineering Attack Strategies and Defence Approaches.†International Conference on Future Internet of Things and Cloud. Vienna, Austria, pp. 145-149, 2016.
TCP/IP Protocols suite Second edition by Behrouz A. Forouzan with Sophia Chung Fegan
Stallings W., "Network Security Essentials: Application and Standards", Printce-Hall, 2000.
Majeed W., "Study of Computer Networks Protection and Simulation by Firewall", Mosul University, 2004.
Al-Obaedey Y., "Study and Implementation Authentication Using Digital Signature", Computers Sciences, University of Mosul, 2004.
Marni, R., Madgul, U. R., & Koyyala, C. T. (2023). OPEN PORT SCANNER TO IDENTIFY OPEN PORTS USING PYTHON. Journal of Science & Technology (JST), 8(12), 17-22.
R. Marni, U. R. Madgul, and C. T. Koyyala, “OPEN PORT SCANNER TO IDENTIFY OPEN PORTS USING PYTHONâ€, Journal of Science & Technology (JST), vol. 8, no. 12, pp. 17–22, Dec. 2023.
Jafarian, J. H., Abolfathi, M., & Rahimian, M. (2023). Detecting network scanning through monitoring and manipulation of DNS traffic. IEEE Access, 11, 20267-20283.
Abu Bakar, R., & Kijsirikul, B. (2023). Enhancing Network Visibility and Security with Advanced Port Scanning Techniques. Sensors, 23(17), 7541.
Dhanya, K. A., Vajipayajula, S., Srinivasan, K., Tibrewal, A., Kumar, T. S., & Kumar, T. G. (2023). Detection of network attacks using machine learning and deep learning models. Procedia Computer Science, 218, 57-66.
Mahmood, Y., & Abdulqader, A. (2021). A platform for porting IPv4 applications to IPv6. International Journal of Computing and Digital Systems, 10, 501-508
DOI: https://doi.org/10.33387/ijeeic.v2i1.9105
Refbacks
- There are currently no refbacks.

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.
| Journal Policies | Submissions | People | Information |
International Journal Of Electrical Engineering And Intelligent Computing
Departement of Electrical Engineering, Faculty of Engineering, Universitas Khairun,
Address: Yusuf Abdulrahman No. 53 (Gambesi) Ternate City - Indonesia
Email: ijeeic.unkhair@gmail.com
 International Journal of Electrical Engineering and Intelligent Computing (IJEEIC), Universitas Khairun This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.
International Journal of Electrical Engineering and Intelligent Computing (IJEEIC), Universitas Khairun This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.




